Introduction:
The incredible growth of the Internet has excited businesses and consumers alike with its promise of changing the way we live and work. But a major concern has been just how secure the Internet is, especially when you're sending sensitive information through it.
Let's face it, there's a whole lot of information that we don't want other people to see, such as:
Credit-card information
Social Security numbers
Private correspondence
Personal details
Sensitive company information
Bank-account information
Information security is provided on computers and over the Internet by a variety of methods. A simple but straightforward security method is to only keep sensitive information on removable storage media like floppy disks. But the most popular forms of security all rely on encryption, the process of encoding information in such a way that only the person (or computer) with the key can decode it.
Computer encryption is based on the science of cryptography, which has been used throughout history. Before the digital age, the biggest users of cryptography were governments, particularly for military purposes. The existence of coded messages has been verified as far back as theMost computer encryption systems belong in one of two categories:
Symmetric-key encryption
Public-key encryption
In symmetric-key encryption, each computer has a secret key (code) that it can use to encrypt a packet of information before it is sent over the network to another computer. Symmetric-key requires that you know which computers will be talking to each other so you can install the key on each one. Symmetric-key encryption is essentially the same as a secret code that each of the two computers must know in order to decode the information. The code provides the key to decoding the message. Think of it like this: You create a coded message to send to a friend in which each letter is substituted with the letter that is two down from it in the alphabet. So "A" becomes "C," and "B" becomes "D". You have already told a trusted friend that the code is "Shift by 2". Your friend gets the message and decodes it. Anyone else who sees the message will see only nonsense.
Public-key encryption
The main problem in Symmetric is the transmission of private key. If user A wants to send a encrypted file to user B, user B should have user A’s private key.For this user A have to send his private key to user B.The transmission of the private key is vulnerable. For this they came to a new concept called Public-key encryption.
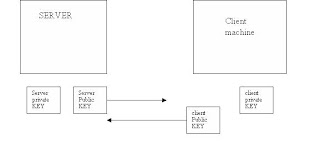
SERVER Client machine Server Public KEY Server private KEY client Public KEY client private KEY
Once the ssl session enabled, the next process is to exchange the key. We need a public key to decrypt the data encrypted by the private key.
The first process is to exchange the public keys’s.
SERVER Client machine Server Public KEY Server private KEY client Public KEY client private KEY
So now the client will have server’s public key, and the server will have client’s public key. So server can decrypt client’s data and client can decrypt server’s data.
SERVER Client machine Server Public KEY Server private KEY client Public KEY client private KEY Server Public KEY client Public KEY
Now the encryption can be attained.
HOW SSL TECHNOLOGY USES ROOT CERTIFICATES IN THE ENCRYPTION PROCESS
When connecting to a web server over SSL, a visitor's browser decides whether or not to trust the website's SSL certificate based on which CA issued the actual SSL certificate. To determine this, the browser looks at its list of trusted issuing authorities -- represented by a collection of Trusted Root CA certificates added into the browser by the browser vendor.


0 comments:
Post a Comment